Auto Amazon Links: No products found. Blocked by captcha.
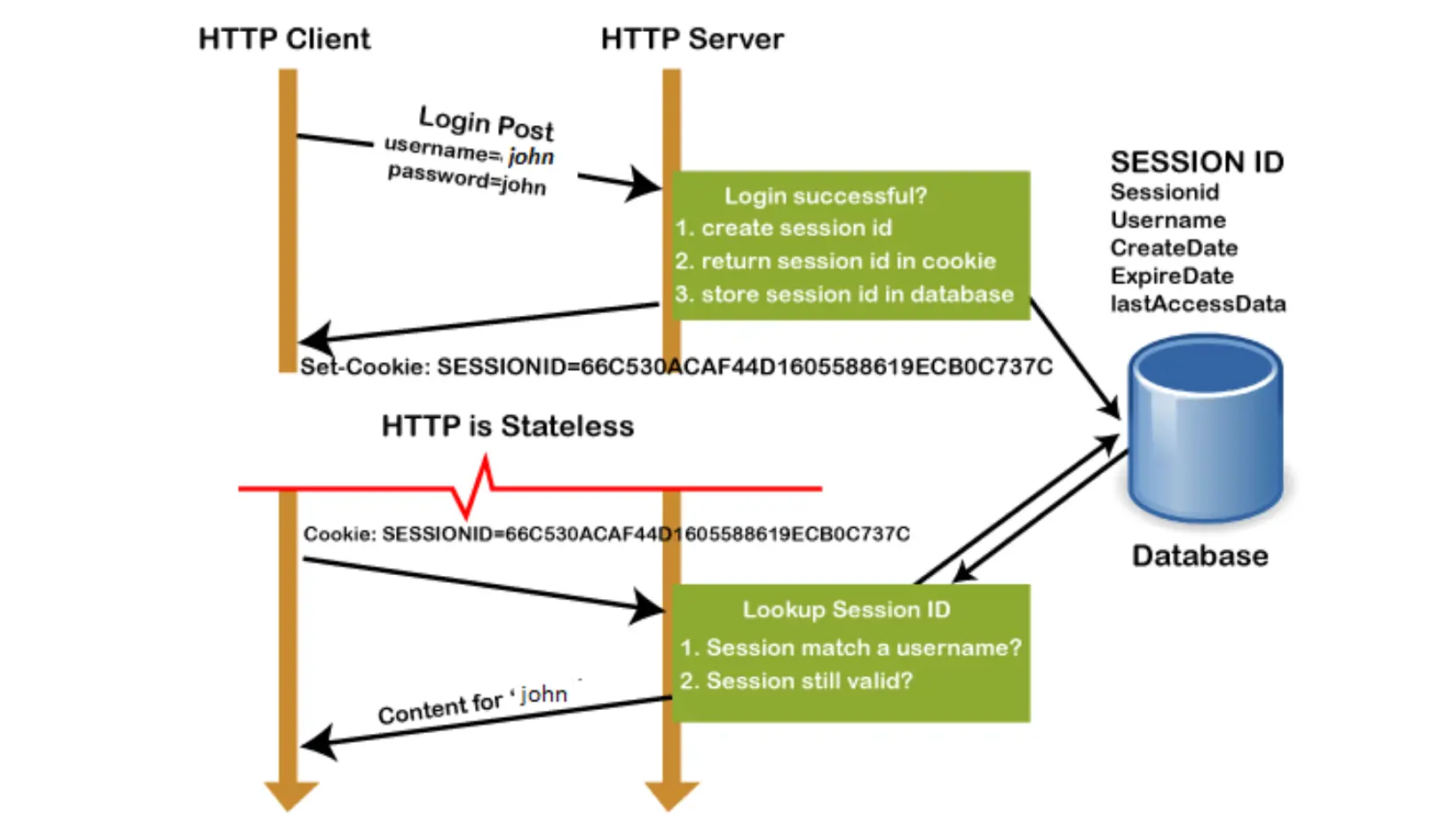
In the realm of web development, ensuring secure and seamless user interactions is paramount. PHP offers powerful mechanisms like sessions and cookies to manage user data while maintaining a robust security infrastructure. In this blog, we’ll explore the essentials of handling sessions and cookies in PHP, along with crucial security considerations to protect against session hijacking.
Managing user sessions
Sessions are a fundamental concept in web applications, allowing servers to maintain user-specific data across multiple requests. PHP sessions work by assigning a unique identifier (session ID) to each user, stored as a cookie on their browser. Here’s a simple example of managing user sessions in PHP:
<?php
// Start a session
session_start();
// Store data in the session
$_SESSION[‘username’] = ‘john_doe’;
// Access session data
echo $_SESSION[‘username’]; // Output: john_doe
?>
Working with cookies
Cookies are small pieces of data stored on the user’s browser. They facilitate the persistence of user information between requests. PHP offers straightforward functions to set and access cookies. Here’s a basic example of using cookies in PHP:
<?php
// Set a cookie that expires in 1 hour
setcookie(‘user_id’, ‘12345’, time() + 3600);
// Access the cookie value
echo $_COOKIE[‘user_id’]; // Output: 12345
?>
Security considerations (e.g., session hijacking prevention)
Ensuring the security of sessions and cookies is critical to safeguard user data. One common threat is session hijacking, where an attacker steals a valid session ID to impersonate a user. To prevent this, developers can take several security measures:
Use HTTPS: Transmitting session data over HTTPS encrypts the data, making it harder for attackers to intercept.
Regenerate session ID: Regenerating the session ID upon login or privilege changes prevents session fixation attacks.
Set secure and HttpOnly flags: Setting the secure flag restricts cookies to secure HTTPS connections, while the HttpOnly flag prevents client-side JavaScript access, reducing the risk of XSS attacks.
Implement session timeout: Configure session timeouts to automatically expire inactive sessions, reducing the window for potential hijacking.
<?php
// Enable secure and HttpOnly flags for cookies
$params = session_get_cookie_params();
session_set_cookie_params(
$params[‘lifetime’],
$params[‘path’],
$params[‘domain’],
true, // Set to true for HTTPS
true // HttpOnly flag
);
session_start();
// Regenerate the session ID
session_regenerate_id();
?>
Conclusion
In conclusion, managing user sessions and cookies is a fundamental aspect of web development in PHP. By understanding how to handle sessions and cookies, along with implementing security measures to protect against session hijacking and other threats, developers can create secure and user-friendly applications. So, embrace the power of sessions, cookies, and security in PHP, and build web applications that provide a seamless and safe experience for users worldwide! Happy coding!
Auto Amazon Links: No products found. Blocked by captcha.